
Executive Summary
Together with 2 other students we contacted CM.com to conduct a penetration test to determine their exposure to a targeted attack. All activities were conducted in a manner that simulated a malicious actor engaged in a targeted attack against CM.com with the goals of:
- Identifying if a remote attacker could penetrate CM.com’s defenses.
- Determine the impact of a security breach on:
- Confidentiality of the company’s private data.
- Internal infrastructure and availability of CM.com’s information systems.
Efforts were placed on the identification and exploitation of security weaknesses that could allow a remote attacker to gain unauthorized access to organizational data. The attacks were conducted with the level of access that a standard customer would have.
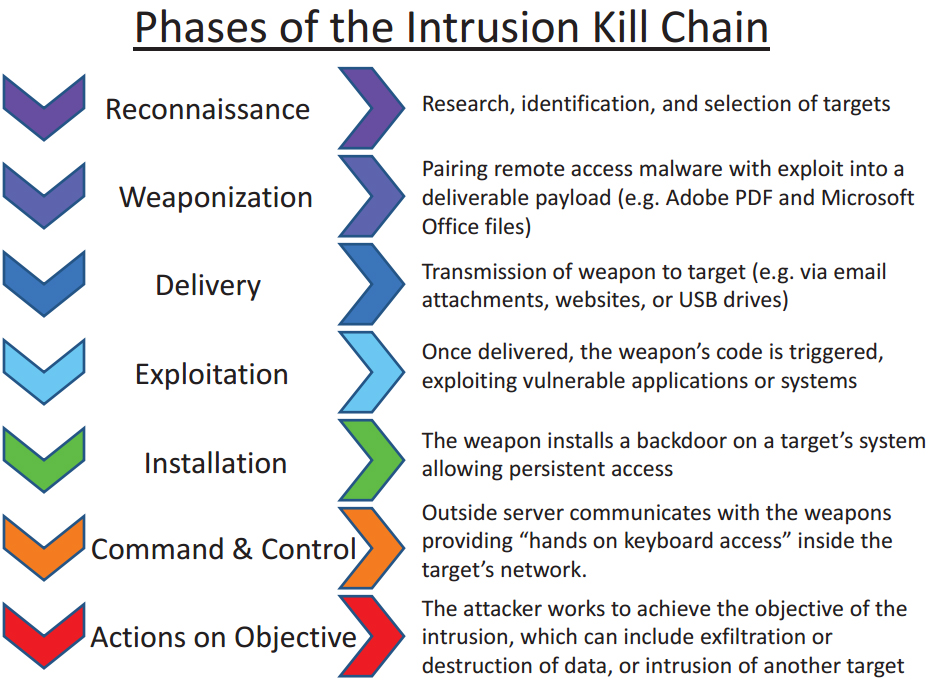
Kill Chain
During the pen test, we used the cyber killcain. We followed and documented every step of the killcain.
Findings
The company is still working through the points in the report.The document is only available for teachers at the moment.